Quishing Attacks: The Emerging Threat in Cyber Security
Cybersecurity threats are continuously evolving, and attackers are always looking for new methods to deceive their targets. One such emerging threat is quishing, short for "QR code phishing." Quishing leverages QR codes to execute phishing attacks, exploiting the growing use of QR codes in various aspects of daily life. This blog explores the concept of quishing, how it works, its implications, and how to protect against it.
CYBER ATTACK
6/2/20243 min read


What is Quishing?
Quishing is a type of phishing attack that uses QR codes to lure victims into providing sensitive information or downloading malicious software. QR codes are increasingly used for various purposes, such as accessing websites, making payments, and sharing information quickly and conveniently. Attackers exploit this trust in QR codes to execute their malicious schemes.
How Quishing Works
Creating Malicious QR Codes: Attackers generate QR codes that embed URLs leading to phishing websites or sites hosting malware.
Distributing QR Codes: These malicious QR codes can be distributed in various ways, such as:
Physical Locations: Posting QR codes in public places, such as flyers, posters, or stickers.
Digital Channels: Sending QR codes via email, social media, or messaging apps.
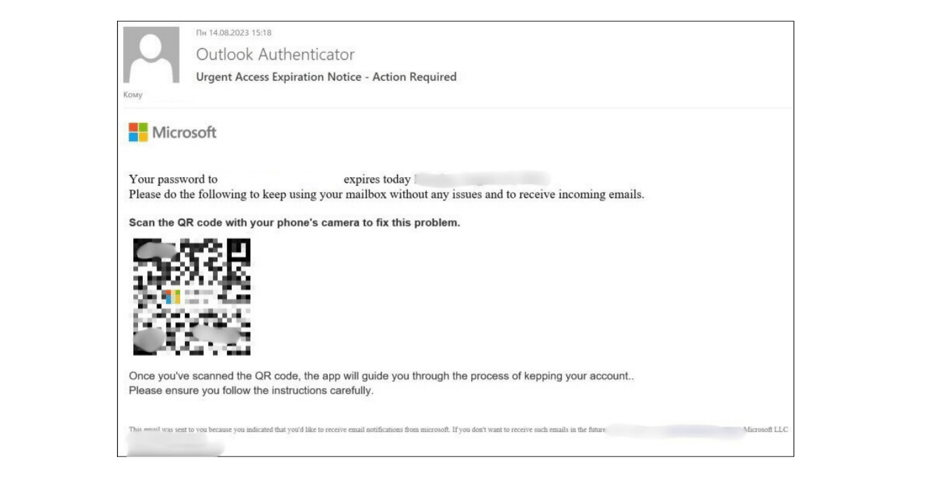
Scamming the Victim: When a victim scans the malicious QR code, they are directed to a phishing site designed to steal personal information, such as login credentials, financial details, or personal identification information. Alternatively, the QR code may prompt the download of malicious software onto the victim's device.
Real-World Examples of Quishing
Restaurant Menus: Attackers place fraudulent QR codes on restaurant tables, leading diners to phishing sites instead of the legitimate menu.
Public Notices: Fraudulent QR codes are posted on public notices, such as fake parking tickets or utility bills, directing victims to phishing websites.
Event Flyers: QR codes on event flyers or advertisements are manipulated to redirect individuals to malicious websites under the guise of event registration or ticket purchasing.
The Implications of Quishing
Quishing can have serious consequences for both individuals and organizations:
Financial Loss: Victims may incur direct financial losses if they provide credit card information or banking details to phishing sites.
Identity Theft: Personal information stolen through quishing can be used for identity theft, leading to long-term repercussions for the victim.
Data Breach: Organizations may suffer data breaches if employees fall for quishing attacks, potentially exposing sensitive company information.
Malware Infections: Scanning a malicious QR code can result in malware being downloaded onto the victim's device, compromising its security and functionality.
Protecting Against Quishing
For Individuals
Be Cautious of QR Codes: Be wary of scanning QR codes from unknown or untrusted sources, especially in public places or unsolicited messages.
Verify Before Scanning: Verify the legitimacy of the QR code's source before scanning it. Look for signs of tampering or unusual placement.
Use QR Code Scanners with Previews: Use QR code scanning apps that provide a preview of the URL before navigating to it, allowing you to verify its legitimacy.
Keep Devices Secure: Ensure that your device's operating system and security software are up to date to protect against malware.
For Organizations
Educate Employees: Conduct training sessions to raise awareness about quishing and other phishing tactics. Educate employees on recognizing and reporting suspicious QR codes.
Implement Security Policies: Establish policies for verifying the authenticity of QR codes before scanning and sharing them within the organization.
Use Secure QR Code Generators: When creating QR codes for business purposes, use reputable and secure QR code generators to minimize the risk of tampering.
Monitor and Respond: Implement security monitoring tools to detect and respond to quishing attempts. Regularly review and audit public-facing QR codes for signs of tampering.
Conclusion
Quishing represents a novel and emerging threat in the realm of cyber security, exploiting the convenience and trust associated with QR codes. As QR codes become more ubiquitous, it is crucial for individuals and organizations to remain vigilant and adopt proactive measures to safeguard against quishing attacks. By staying informed, practicing caution, and implementing robust security practices, we can mitigate the risks posed by quishing and other phishing attacks.
Cyber Guard Forte
